Secure 128-bit SSL communication
All communications between E-Storage Backup Server and your computer are transported in a 128-bit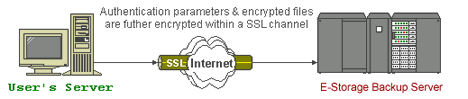
SSL (Secure Socket Layer) channel. Although all your backup files travel through a public network (internet), eavesdroppers have no knowledge of what has been exchanged.
Backup data are securely encrypted
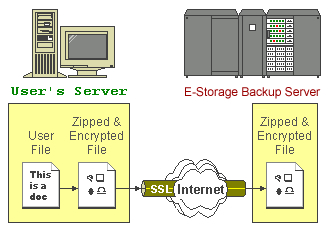
All of your files are first zipped and encrypted with your defined encrypting key before they are sent to E-Storage Backup Server. To all people but you, your files stored on E-Storage Backup Server are no more than some garbage files with random content.
We donít keep your encrypting key
The encryption key used to encrypt your files resides only on your computer and is known only to you. It is never transmitted anywhere across the network. If this key is lost, all backup files can never be recovered. Therefore, although we have access to all files you stored on our backup server, we have no knowledge of the content of the files you stored.Reminder : Please make sure you write down you encryption key in a safe place where it will never be forgotten. Otherwise, you will never be able to recover your backup files.
Best encryption algorithm is used
Currently, the algorithm that we are using to encrypt your files is 128-bit Twofish. It is a block cipher designed by Counterpane Labs. It was also one of the five Advanced Encryption Standard (AES) finalists chosen by National Institute of Standard and Technology (NIST). It subjects to frequent public reviews but no known attack against this algorithm has been reported.Require 8.77 x 1017 years to crack the 128-bit encryption A 128-bit key size has 2128 or around 3.4 x 1038 possible combination. Even if you have the world best super computer, ASCI White, SP Power3 375 MHz manufactured by IBM as of November 2000, it would take 8.77 x 1017years to test all combinations. Assuming your have the super computer, ASCI White, SP Power3 375 MHz has 8192 processors which totals a capability of 12.3 teraflops (trillions of operations/second), available to you. Also it just needs one computer operation to test a possible combination (which is already faster than what it can do). To use brute force attack (checking all combinations) on this encryption algorithm. It would take:
3.4 x 1038
-------------- seconds ~ 2.76 x 1025sec
12.3 x 1012
i.e. 876530835323573935 years or 8.77 x 1017 years to successfully try all combinations. Let alone ASCI White cannot process as fast as what described here. You can be sure that your data stored on our server is 100% secured.